ANOTHER YEAR, ANOTHER RUN OF ATTACKS
Advancements in technology are occurring at an increasingly dizzying pace. New technologies emerge to join the ranks alongside ‘new and improved’ functionalities of existing ones….and all the while, increased adoption of these technologies has led to an exponential growth of data breaches. Verizon’s 2018 Data Breach Investigations Report listed nearly 2,200 data breaches and more than 53,000 total cybersecurity incidents reported from 65 countries from April 2017-March 2018 – an average of six breaches and 145+ incidents EVERY DAY. However, this next statistic puts the issue into perspective whether you’re reading this in your office, sitting in a traffic jam, on a plane, or at home with your family. Look to your left and see one person. Then look to your right and see two others. By the law of averages, one of those three people experienced a compromise of their personal information in the U.S. within the past year.
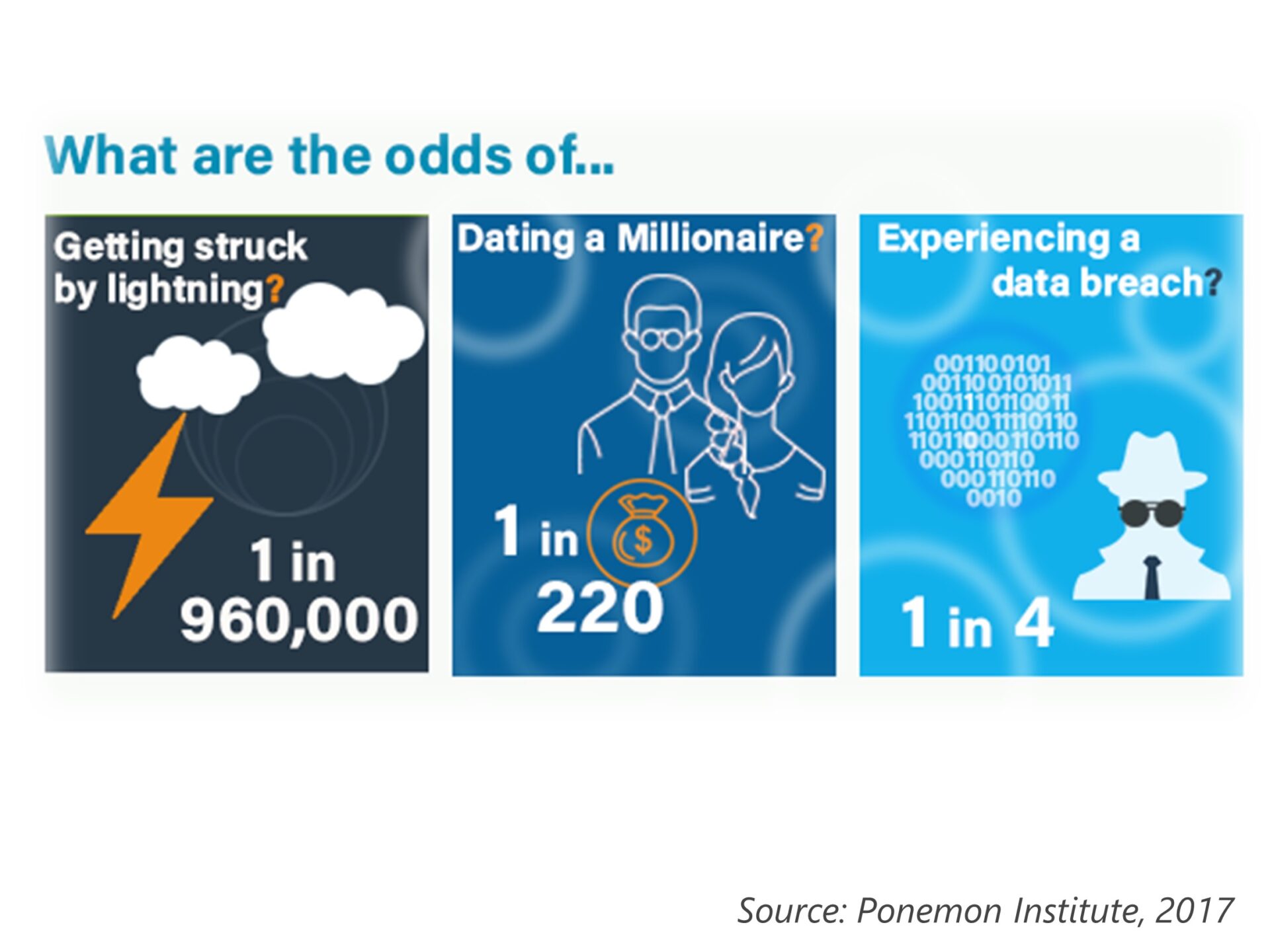
The problem is real, the problem is persistent……and it gains momentum the more technology becomes intertwined with the fabric of our everyday lives.
The ever-growing trend of data breaches is in full force as several high-profile cyberattacks have crippled networks across the world. In early 2019, Canada’s Olympia Financial Group Inc. announced that it was hit by a ransomware attack, leading to an investigation into personal information that may have been compromised (the inquiry is ongoing at press time) and severely affecting its business operations while it secures its IT systems. Another episode hit close to home here in Northeast Ohio: a malware attack installed on City of Akron servers – resulting in a disruption of the city’s 3-1-1 information line, with a ransom demand in exchange for its unlocking.
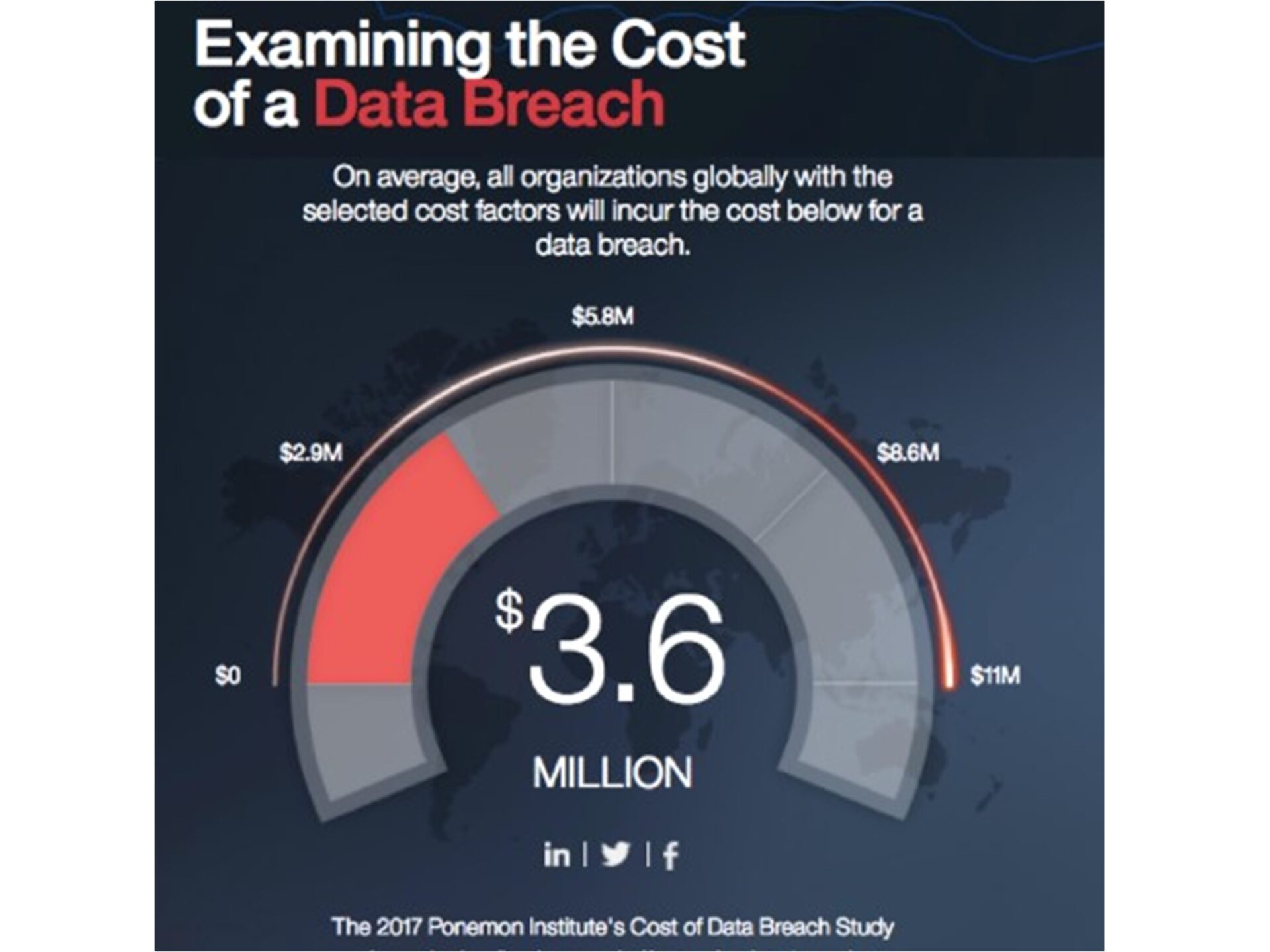
All organizations at some point will have to deal with a cybersecurity incident that can cause business disruption, lost productivity, lost data and lost money (the Ponemon Institute’s 2017 Cost of Data Breach Study put the average cost of a data breach at $3.6 million, with the cost-per-compromised-record at $141).
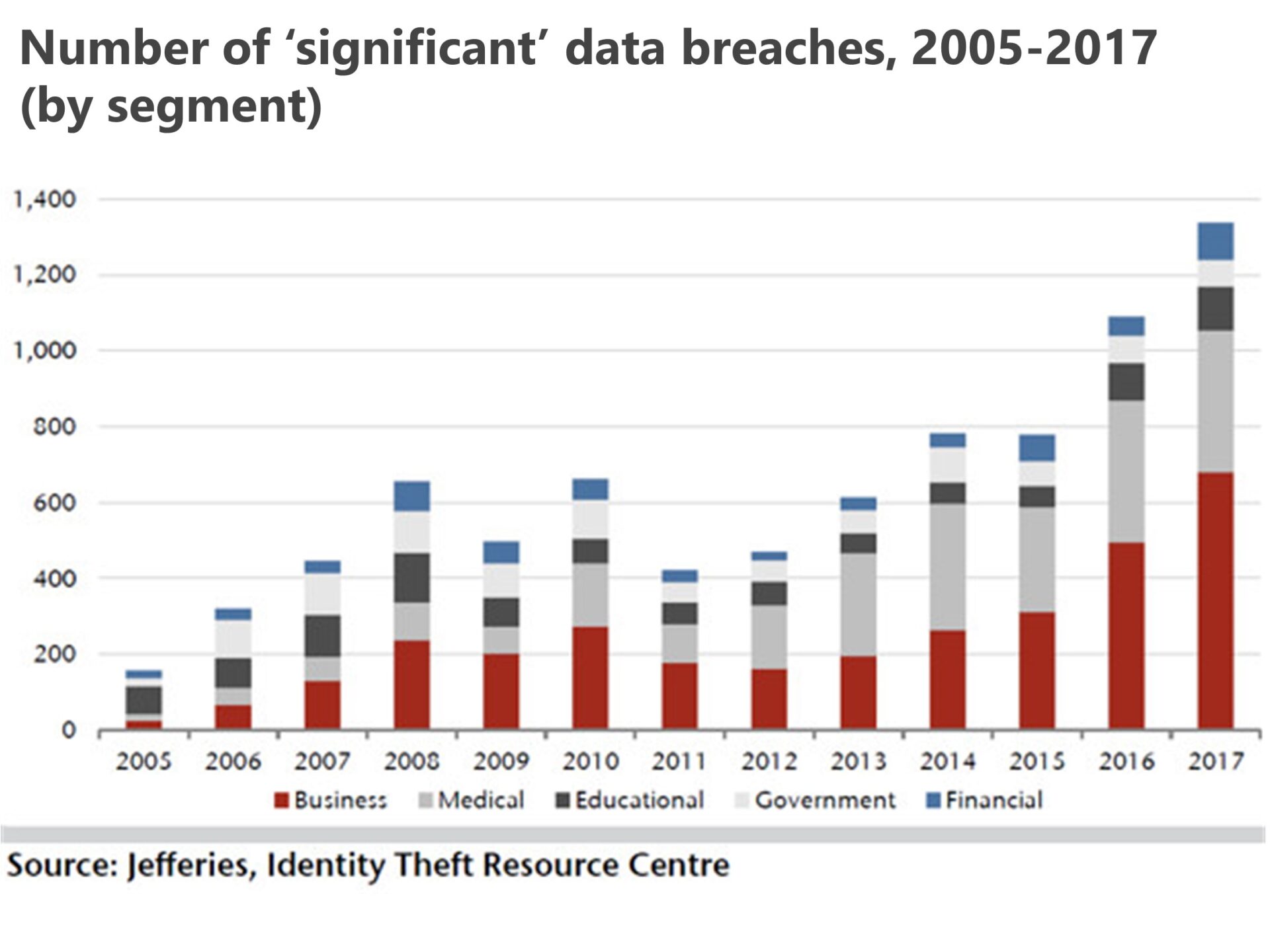
THREATS COME IN MANY FORMS, FROM MANY DIRECTIONS
Cybercrime has grown into an estimated $600 billion industry worldwide. With every new functionality, feature and access port to technology comes with new opportunities for cyberthieves and hackers to enter and corrupt networks. Some of the most common types of attacks are:
- Hacking/Malware: malicious software including spyware, ransomware, viruses and worms
- Phishing: the sending of fraudulent communications that appear to come from a reputable source, typically via email
- Man-In-The-Middle (MitM) Attacks (AKA Eavesdropping Attacks): occur when attackers insert themselves into a two-party transaction, most commonly through unsecure public Wi-Fi networks or malware
- Denial-of-Service Attacks: flooding systems, servers or networks with traffic to exhaust resources or bandwidth, leading to a fulfillment disruption of legitimate requests
- Structured Query Language (SQL) Injection: occurs when an attacker inserts malicious code into a server that uses SQL and forces it to reveal proprietary information
- Zero-Day Exploit: hits after a network vulnerability is announced but before a solution is implemented
Many of TEC’s customers have noticed an alarming trend of data breaches affecting partners and suppliers within their industries. “We have several customers and suppliers who have been hit by ransomware,” said an IT executive with a customer that is a global logistics solutions provider. “These are multi-billion-dollar companies, and when they suffer an outage (due to a breach), it impacts us directly.”
With these security threats hitting all industries, a dynamic cybersecurity strategy is a prerequisite for a company to protect itself. “Seeing these breaches all around our business forced us to escalate our security awareness and implement a stronger cybersecurity plan,” said our customer. “We need to have peace of mind that, day in and day out, our information is safe.”
Want to learn how you can take steps to protect your data from cyberthreats? Here are five quick but helpful tips to keep your IT safe in 2019:
TIP #1: IMPLEMENT A CYBERSECURITY TRAINING PROGRAM
In its survey of over 1,000 small business owners and C-level executives, Information security company Shred-It’s 2018 State of the Industry Report found that 47% identified human error (such as unintentional loss of a device or document, leaving a device unlocked while unattended, etc.) as the catalyst of a cybersecurity breach at their organization. Furthermore, the Ponemon Institute reports that two out of three threat incidents are caused by employee or contractor mistakes. This evidence clearly indicates a disconnect between where employees currently sit in their grasp of secure technology practices and where they should be.

In 2019, make it a priority to integrate a cybersecurity awareness and training program into your organization processes. Some ideas for protocol implementation:
- Create a policy about the use of personal email accounts and social media platforms on work devices
- Hold quarterly training seminars for recognizing threat indicators, app installs and updates, and Virtual Private Network (VPN) setup and usage when working remotely
- Make any training programs a core part of your onboarding program for new employees
- Bring in guest cybersecurity speakers and instructors for lunch & learns (contact TEC if you’d like to discuss, as we hold many of these)
- Schedule regular data access audits to ensure that the right employees have appropriate access to information, and that ex-employees who longer work at your company don’t have access
TIP #2: GET A FIREWALL SOLUTION THAT PROTECTS YOUR ENTIRE NETWORK
- How effectively does your firewall monitor your network’s incoming and outgoing traffic?
- How well does it prevent viruses and other threatening intrusions?
- Does your firewall properly manage bandwidth so that your network can operate at peak performance?
- Do its identity and access management protocols consistently weed the bad users out?
Your network’s firewall is the dataflow and coverage epicenter of your IT. It needs constant monitoring to ensure that your entire network is both efficient and secure against advanced threats.
Cisco’s Next Generation Firewall:
- Offers deep visibility into who’s using which applications on your network
- Filters URL addresses to identify and protect against traffic from known malicious websites
- Leverages Cisco’s Talos Intelligence Group (one of the largest commercial threat intelligence teams in the world) which constantly analyzes threat data, creating security protections to further fortify the firewall to prevent breaches
Cyberattackers are getting smarter every day, and your firewall needs to have every network entry point protected.

TIP #3: MAKE SURE YOUR EMPLOYEES ARE PROTECTED — REGARDLESS OF WHERE THEY’RE LOCATED OR CONNECTING
In TEC’s October 2018 Collaboration in Workplaces blog, we dove into the shifting of workplace dynamics from only office headquarters to a structure involving multiple satellite/home locations, employees with non-traditional hours, and more mobile and remote workspaces – all requiring real-time connectivity on a multitude of devices – computer workstations, laptops, phones, and tablets. Protecting your information everywhere your employees go on your network becomes exponentially more difficult when they’re connecting in a myriad of places, on an increasing number of devices. Will your cybersecurity setup protect against a data intrusion over an unsecured Wi-Fi network at the local coffee shop? At an an airport gate? In an employee’s hotel room while traveling on business? While answering emails at their child’s soccer practice?
Not knowing the answers to these questions leaves a huge gap in your cyberdefense……and creates opportunities for breachers to leverage a singular entrypoint to create havoc for your entire organization.
Cisco’s solutions give employees top-level protection regardless of where they’re located or connecting.
- Cisco’s Umbrella Cloud Security platform constantly monitors internet activity patterns to uncover current and emerging threats and malicious destinations — before a connection is ever established, so risk to your network is minimized.
- Cisco’s Email Security solution protects against email threats by blocking suspicious and malicious content, links and attachments, and analyzes messages for sensitive and proprietary material prior to leaving the organization. The results: more spam is caught, false positives are minimized, and users enjoy heightened protection.
- Cisco Advanced Malware Protection (AMP) monitors files 24/7 on all end-user devices and identifies malware before it can damage networks……making operations easier, faster, and safer with minimized inefficiency and downtime.
TIP #4: BE MORE DILIGENT IN CONDUCTING ONGOING INTERNAL THREAT TESTS
TEC can help train your employees to identify cyberthreats that attempt to access your network via their endpoints.
Regular phishing simulation tests are a turnkey way to test the effectiveness and recognition of phishing attempts. Such attempts (which are becoming more sophisticated, especially with the explosion of social media platforms) can be successfully stifled using a variety of approaches.
Additionally, penetration tests – commonly referred to as ‘pen’ tests – should be a dedicated part of your company’s continuing cybersecurity plan (this is one of several options among TEC’s roster of Managed Services, which takes many of the details of maintaining and monitoring your IT off of your plate so you can concentrate on growing your business). A planned simulated attack on a system using the same tools and techniques that a cyberthief would, it reveals the strengths and vulnerability points in a cyberdefense plan. Such tests should be performed at least quarterly to maintain optimal security levels. The Payment Card Industry Data Security Standard mandates a regular testing schedule, including immediately after any system changes or upgrades.
TIP#5: CONSIDER USING SINGLE SIGN-ON OR MULTI-FACTOR AUTHENTICATION TO BUOY PASSWORD SECURITY
LinkedIn’s 2012 data breach, which resulted in nearly 7 million encrypted passwords posted to a Russian crime site, yielded some interesting insights. Among them: more than one in three were classified as ‘weak’ (either an easily guessed one – ‘123456’ and ‘password’ are still routinely among the most commonly used, a recycled one, one that can easily be decoded, etc.)
Look into the advantages of Single Sign-On (SSO) and Multi-Factor Authentication (MFA) resources, which exist for this express purpose. SSOs leverage other trusted sites to verify users’ identities, then allows them access with a single ID and password (which, because they are verified by other trusted sites, are not held in that site’s database). MFAs grants the user access to a network only after successfully presenting two (or more) pieces of evidence from among:
- Something they know (i.e. a password)
- Something they have (i.e. an access card, chip, etc.)
- Something they are (i.e. fingerprint, voice, etc.)
Duo Security is an example of an effective, easy-to-use and affordable SSO/MFA solution that can significantly reduce your risk of a user-generated data breach.
IN CONCLUSION
Cyberattacks do not happen in a vacuum; many variables come into play at every turn – on both the attacker and target sides – that make the dynamic a living, breathing organism that morphs with every advancement in technology. Therefore, it is CRITICAL to combat threats with a steady, ongoing campaign to ensure you’re never caught with your guard down.
TEC Communications is a Cleveland-based Cisco Premier Certified Partner – in fact, the first Cisco technology partner in Northern Ohio – and trusted IT solutions provider celebrating its 40th Anniversary in 2019. Go to http://www.tec4it.com or call us at 440.333.5903 to find out how TEC Communications can help you identify, combat and prevent attacks on your sensitive data

